Threat Detection & Monitoring
The Threat Detection & monitoring is the first layer of defense. It includes the deployment of an array of sensors that monitors the organizational data and detects threats.
SOC – Security Operating Center
Our innovative model of cyber-secuity protection services, is operated from a sophisticated Security Operating Center – SOC. It is manned by security experts, analysts and architects 24/7, ready to respond to any threat. The SOC utilizes advanced tools to detect cyber-attacks, including alert mechanisms, detection tools and comprehensive reports, providing the team of security experts an up-to-date status and allowing rapid response to threats.
- Advanced cyber security tools to continuously monitor and control the organizational environment
- Monitoring and analysis of the network traffic to detect anomalies
- Advanced threat detection and management
- Intrusion Detection System (IDS)
- Event analysis and cross-reference data against global thread exchange database
Threat Exchange – Knowledge is Power
Our SOC receives constant updates from a global cyber-security center called Open Threat Exchange (OTX). This center bundles information from over 8,000 sources, deployed in 140 countries.
The global cyber-security center is one of the largest in the world, providing security experts and researchers with a platform to gather and share information on cyber-attacks, in order to quickly respond to new threats.
Research labs of some of the world's largest technology companies relay information to this threat exchange center, among those are: HP, Intel Security, Blueliv, Columbus, GoGrid, RiskSense and others.
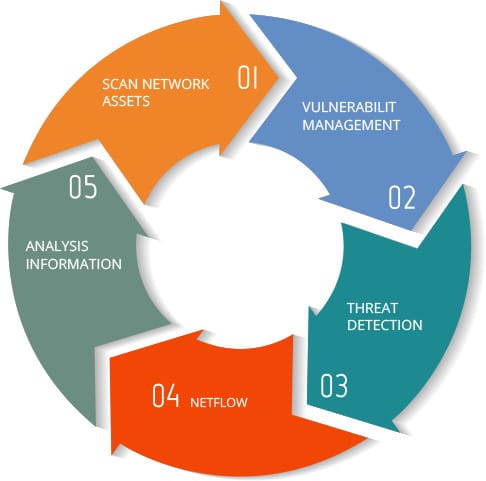
Continuous Monitoring & Threat Detection
Our monitoring technology works methodically and continuously to enable full scan of the organizational array, using these phases:
Network Assets Scan
Mapping, locating and identifying all devices connected to the organizational network, to establish a secure perimeter
Vulnerability Management
Detection of weak spots and vulnerabilities, followed by a detailed report of these and recommendations given by experts for corrective measures.
Threat Detection
Rapid identification of any threat, whether it is network based (NIDS), or host-based (HIDS), along with thorough details of the threatened component.
NETFLOW - Traffic Monitoring
Log collection and analysis, along with analysis of network traffic, providing a broad and in-depth insight of network-based events and threats.
Information Analysis & Cross-Referencing
Analyzing and crossing-referencing gathered information with all sources of information, including information form the Open Threat Exchange center, enable us to rapidly understand the nature of the threat and respond promptly.
Reports
These five phases of monitoring enable strict control over any and all network traffic at any given time. Our team of security experts and analysts draw insights from this information, and translates it into proactive measures to strengthen and enhance the organizational security network.
We provide our clients with custom-suited reports including details of connections, events, alerts and reports to comply with regulation requirements, such as PCI, ISO-27001, and others.
We operate a personal information portal at your disposal to view the current status of everything happening in the organizational network, along with a summary of security events at any given time.


 - בניית אתרים
- בניית אתרים